How they actually work, where they break, and why hybrid DAST + code‑intelligence is pulling ahead
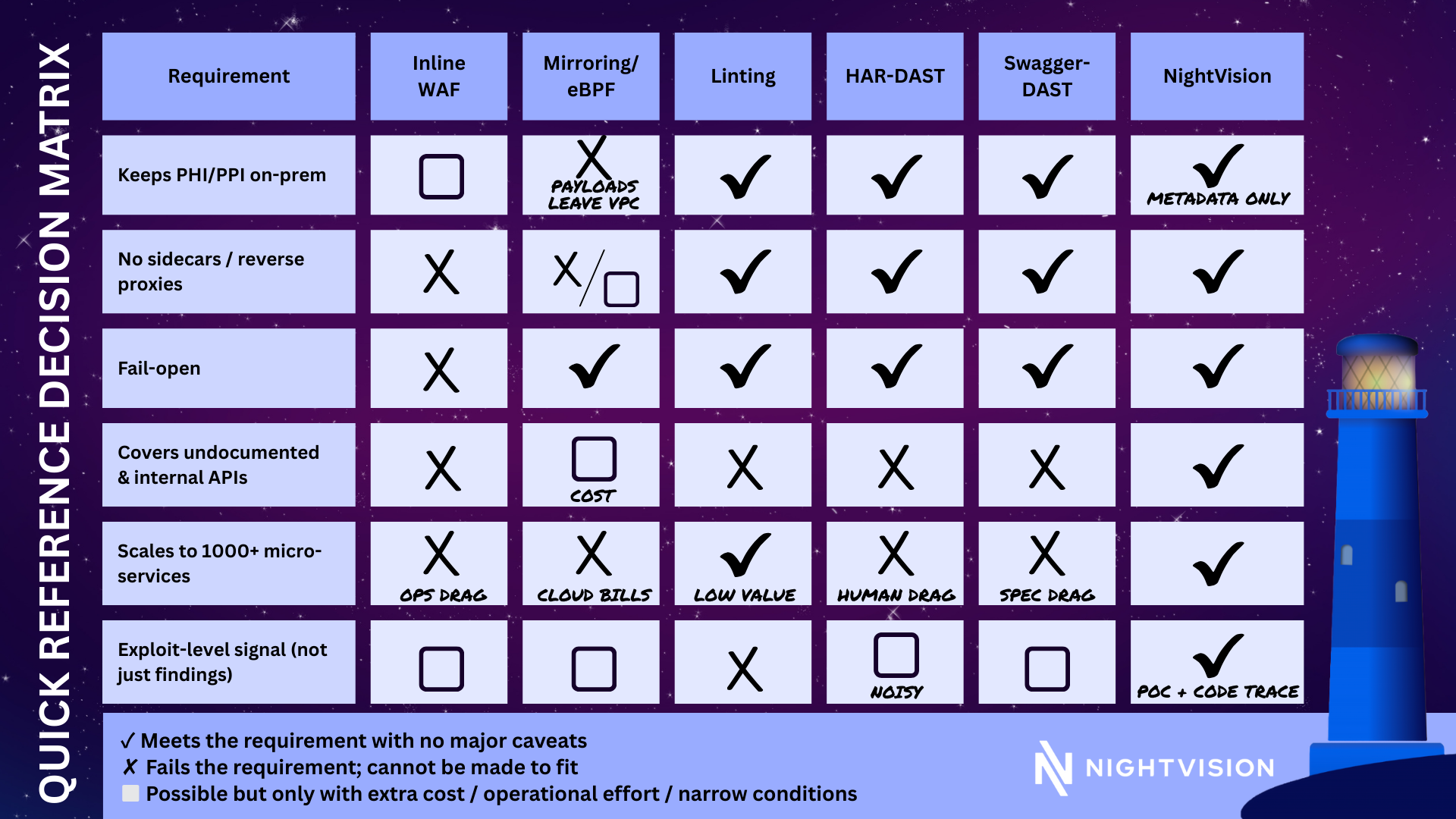
1. Inline WAF / “API‑Runtime Protection”
How it works – Terminate TLS, parse every request, apply ML‑backed rules, block on the wire.
When it helps – Quick win for a single internet‑facing gateway.
Hidden costs & deal‑breakers
- Needs full reverse‑proxy insertion, every edge, every region.
- Does not fail open; if the proxy dies your API is offline.
- Blind to internal and service‑to‑service traffic (usually >80 % of calls).
- $‑per‑TPS adds up fast once you go beyond the public ingress tier.
2. Traffic Mirroring & eBPF/Sidecar Telemetry
How it works – Clone packets with VPC Traffic Mirroring or an eBPF sidecar; ship raw streams to the vendor’s cluster for deep analysis.
When it helps – You need flow visualisation for a short forensic project.
Hidden costs & deal‑breakers
- Up to 50 TB/month duplicated traffic for a mid‑size estate, storage and egress bills dwarf the licence.
- Full payloads (tokens, PHI, PCI) leave your boundary → automatic GDPR & HIPAA red flag.
- Non‑K8s workloads? Service mesh disabled? Agent install blockers halt rollout.
3. Spec Linting (“Swagger Hygiene”)
How it works – Run an open‑source linter against OpenAPI docs; flag inconsistent verbs, auth gaps, data‑type mismatches.
When it helps – Mature external developer programme with pristine specs.
Hidden costs & deal‑breakers
- Finds spec defects, not actual vulns.
- Useless for the ~70 % of endpoints that have no Swagger at all.
- Zero runtime signal: business‑logic flaws, auth bypass, broken object‑level auth never surface.
4. Legacy DAST via HAR Playback
How it works – Developers record traffic (HAR), feed it to a scanner that replays requests with OWASP Top‑10 payloads.
When it helps – One‑off pre‑prod scan of a single service, when you have the people to script a clean capture.
Hidden costs & deal‑breakers
- Continuous coverage impossible without end‑to‑end test harnesses, dev teams rarely have bandwidth.
- Priced per‑scan or per‑endpoint, so portfolios with 1000+ micro‑services explode the budget.
- Still bound to existing documentation (or HAR) → shadow & zombie APIs remain invisible.
5. “Contract‑Aware” DAST (Swagger‑Driven)
How it works – Import Swagger, crawl endpoints, fuzz parameters, report exploitable findings.
When it helps – Teams disciplined enough to ship perfect specs before code hits staging.
Hidden costs & deal‑breakers
- Requires accurate, complete spec first. In reality, most prod APIs are undocumented.
- Misses internal gRPC/GraphQL or event‑driven surfaces that aren’t HTTP‑REST.
6. Hybrid Code‑Intelligence + DAST (NightVision)
How it works –
- API eNVy statically walks source, framework routes, IaC, and tests to generate a full API spec, no dev tickets, no sidecars, no data egress.
- The generated contract seeds a DAST engine that launches authenticated, stateful attacks (SQLi, BOLA, mass‑assignment, IDOR, broken auth flows).
- Verified findings are traced to the exact file/line; GitHub Security Alert created with PoC and fix guidance.
Why it clears the enterprise bar
- Fail‑open – All scanning happens out‑of‑band; production traffic path untouched.
- Zero data residency risk – Only metadata/spec leaves the estate; no tokens, no PHI.
- Full coverage – Internal, external, even undocumented endpoints are tested automatically.
- Dev adoption – Three CLI commands; no reverse proxies, no sidecars, no HAR gymnastics.
- TCO– One platform covers discovery and exploit‑level testing; no second vendor for visibility, no seven‑figure packet‑capture bills.
What to Ask Every Vendor
- Show me the full data path. Where do tokens and payloads land?
- Describe your failure mode. Does production traffic drop if your sensor dies?
- How do you handle un‑documented endpoints? If the answer is “ask devs to write Swagger,” keep walking.
- What’s the monthly AWS bill for a ___ Gbps workload? If they won’t estimate, you already know.
- How long from git clone to first exploitable finding? Time‑to‑signal is the best reality check.
NightVision’s dynamic + static hybrid alternative
NightVision’s approach to the task of API security begins with using DAST to directly challenge APIs through synthetic attacks. In both cases, NightVision is on the lookout for bad behavior patterns.
- First, NightVision uses a static analysis engine with a discovery technology called API eNVy to create a complete, all-inclusive API specification file. This file, rather than a separately produced Swagger UI file, documents all the endpoints in the entire system, while also being human-readable. This enables the file to stand on its own as a complete catalog of an organization’s entire API, which may be useful in merger operations or for insurance or compliance purposes.
- Using the file generated by API eNVy, NightVision’s DAST scanner identifies all the listed API endpoints and sends malicious data to those endpoints to test for attack vulnerability.
- When vulnerabilities are discovered, NightVision then utilizes its LLM to produce human-readable warnings and guidance, giving developers not only the information they need to eradicate bad API behavior before their code proceeds to production, but also the knowledge and instructions they require for how to go about it.
These are the critical distinctions between NightVision’s strategy and other approaches to API security. Other methods protect against the effects of bad API behavior. Used collectively, those methods may be reasonably effective, yet only up to a point. NightVision gives your developers the tools, the information, and the support they need to stop the bad behavior altogether.
Bottom Line
Most “API‑security” products still guard only what they can see, the documented, internet‑facing slice of your estate. Meanwhile, threat actors happily pivot through the internal, the forgotten, and the mis‑documented.
NightVision flips that problem on its head by building the missing map from code, then attacking everything on the map, without rerouting traffic, siphoning data, or drowning teams in false‑positive noise.
When the boss asks why you’re not buying a proxy, an eBPF agent farm, and a separate discovery tool, you can copy‑paste:
“Those stacks either break our data‑residency rules, fail closed, or leave 80 % of our estate untested. NightVision gives us full‑estate coverage, exploit‑level proof, and zero production drag, at a price that isn’t 50 TB of mirrored traffic per month.”
Schedule a NightVision Demo


.svg)





.svg)